How Can Hackers Hack WiFi Networks?
To hack WiFi passwords, hackers take two vastly different approaches. Some hackers rely on low-skill attacks that exploit weak passwords and naïve users, while others can execute highly technical attacks using cutting-edge exploits and sophisticated, custom-made tools.
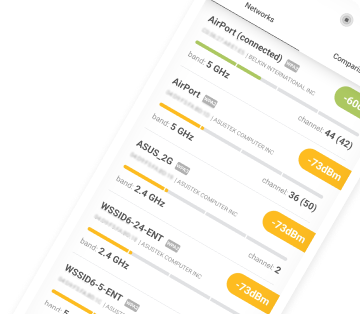
Without encryption, the traffic on a WiFi network can be captured and analyzed by everyone within the range of the network. If you’re curious how far can a hacker be from your home router and still have a strong-enough signal to hack your WiFi, you can download NetSpot, an easy-to-use WiFi analysis tool. With NetSpot, you can instantly see whether your WiFi network is sufficiently encrypted to withstand a targeted attack.
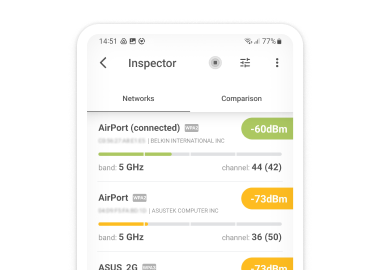
Strong WiFi encryption, such as WPA2, has become an absolute necessity, but even the strongest encryption protocol can be undermined by a weak password. Yes, it can be a drag to remember a ten-digit alphanumerical string of gibberish, but the consequences of a successful WiFi hack can be devastating.