Powerful advanced tool for multiple Wi-Fi networks Surveys, Analysis and Troubleshooting.
WPA3: The Cutting-Edge of WiFi Security
To be effective, WiFi security needs to keep up with rapidly evolving cyber threats, which is where the WPA3 standard comes in to make private and public networks alike more resilient.
To prepare for this new level of protection, homes, and businesses should analyze their network’s coverage with tools like NetSpot to offer maximum coverage when installing new routers and WiFi extenders.
What is WPA3
Every generation of computer technology spawns both new promise and new problems. When the first universities allowed users to connect to powerful mainframes, unruly students found ways of accessing other student’s information to play pranks on each other, requiring the creation of password protection and access rights.
Today, computers and wireless networks occupy every aspect of life, from schools, hospitals, businesses, libraries — even coffee shops and buses offer WiFi access. But with all this access, there is the need for WiFi network security. A person connecting via their laptop could be transmitting the passwords to their bank account over the air for a hacker to pick up.
The biggest problem with allowing access to a local WiFi network isn’t just WiFi encryption, but how to register devices onto the WiFi network. If there’s a shared password, then anyone who shares that with another person or writes it down runs the risk of unauthorized users getting access to the network.
For those old enough, remember that scene from the movie “Wargames” where Matthew Broderick’s character would purposely get detention so he could find the network’s password written down in a secretary’s desk? Hackers use the same technique when someone writes down the WiFi password on a Post-It on their desk to get access into the network and start capturing packets.
WPA3 security is designed to help prevent that. Rather than relying on shared passwords, WPA3 signs up new devices through processes that don’t require the use of a shared password.
This new system, called Wi-Fi Device Provisioning Protocol (DPP), works by transmitting how to gain access to the system without transmitting a password into the air. With DPP, users use QR codes or NFC tags to let devices onto the network. By snapping a picture or receiving a radio signal from the router, a device can be authenticated to the network without sacrificing security.
WPA3 encryption is geared to be better than previous iterations of WiFi technology. First, like the move of browsers Google Chrome and Firefox to warn or outright block users from connecting to insecure web servers, WPA3 security discards older encryption mechanisms in favor of ones that have not been broken.
Granted, nothing lasts forever in the world of security, but WPA3 Encryption is covered by 256-bit Galois/Counter Mode Protocol (GCMP-256) so that makes breaking through the encryption harder.
How big is a number like 256-bit? Previous encryption algorithms worked with 128-bit encryption. In Math terms, that’s 3.048 x 10^38 — that’s 3 followed by 38 zeros after it — that’s how many calculations a computer would have to make to even guess at what the encryption key is. 256-bit encryption? That’s 1.15 x 10^77 — 1 with 77 zeroes following after it.
There is a fewer number of atoms in the known universe compared to that number. There are fewer episodes of Judge Judy than that number. Fewer times that someone has asked, “Explain the plot of the movie Inception.”
It’s a big number.
When transferring encryption keys between the router and devices, WPA3 WiFi Security uses 384-bit Hashed Message Authentication Mode so both the device and the router confirm that they can connect, but in a way where even if someone picks up the communication between them they can’t figure out what they original encryption key is.
It’s like the Navajo code talkers back in World War II who used codes while speaking a language no one else in the world understood. Even if a third party could pick up the radio signals, it wouldn’t make any sense to them. Even if they also happened to speak Navajo, they’d have to know the additional code structure underneath that to understand what the message actually meant.
This is how WPA3 keeps communications safe — with better encryption, better ways of setting up that encryption, and methods that keep people connecting to the network from knowing the passwords that have them on the network.
Main Forms of WPA3
To address the needs of different categories of WiFi users, WPA3 comes in several main forms. Understanding the differences between them can help you take full advantage of its security features.
WPA3 Personal
Home users are expected to use the WPA3 Personal form, which relies on passphrase-based authentication. This form offers a familiar user experience but a vastly superior level of protection against brute force cracking thanks to Simultaneous Authentication of Equals (SAE).
WPA3 SAE replaces the Pre-Shared Key (PSK) authentication method used in previous versions of WPA to generate a key that’s completely unique to each authentication.
As a result, attackers lose the ability to perform off-size attacks on captured data packets to overcome the defenses of the target network. What’s more, members of the same network can’t snoop on the traffic of other members.
WPA3 Enterprise
The WPA3 Enterprise form extends the solid foundation provided by WPA2 Enterprise by making it mandatory to use Protected Management Frames (PMF) on all connections. This security feature protects against such dangerous attacks as honeypots and eavesdropping.
To better protect the most sensitive data, WPA3 Enterprise can optionally operate in a special 192-bit mode. This mode isn’t necessary to achieve a satisfactory level of security, but all enterprises are encouraged to take advantage of it to enjoy the best protection available.
WiFi Enhanced Open
Unencrypted public WiFi networks represent a huge threat, and many WiFi users are not even aware of how dangerous they can be. WiFi Enhanced Open addresses this problem by providing unauthenticated data encryption based on Opportunistic Wireless Encryption (OWE).
Unauthenticated data encryption preserves the convenience of public WiFi networks because no passphrases are involved, so there’s really no reason not to enable it.
WPA3 Personal vs WPA3 Enterprise
When deciding between WPA3 Personal and WPA3 Enterprise, the target environment is the most important factor. While regular home users can theoretically benefit from the superior protection provided by WPA3 Enterprise and its 192-bit mode, the increased setup difficulty outweighs the benefits.
What are WPA3's weaknesses?
Wi-Fi Protected Access 3 (WPA3) was introduced to enhance the security of wireless networks by addressing vulnerabilities found in its predecessor, WPA2. However, like any security standard, WPA3 has its weaknesses and vulnerabilities that attackers can exploit. Here are some of the key weaknesses identified in WPA3:
- Dragonfly Handshake Vulnerabilities: WPA3 implements a new handshake protocol called Dragonfly (or Simultaneous Authentication of Equals, SAE) intended to offer protection against offline dictionary attacks. However, researchers have found vulnerabilities in this handshake process that could potentially allow attackers to perform side-channel attacks, such as timing or cache-based attacks, to retrieve information about the password being used.
- Downgrade Attacks: While WPA3 is designed to be more secure than WPA2, networks often support both standards to ensure backward compatibility. This opens up the possibility for downgrade attacks, where an attacker forces a device to connect using the less secure WPA2 protocol, thereby bypassing WPA3's security enhancements.
- Implementation Flaws: The security of a system also depends on how well the security protocols are implemented. Early on, some implementations of WPA3 were found to be susceptible to various attacks due to flaws in how the Dragonfly handshake was implemented. These issues allow attackers to bypass WPA3's security mechanisms under certain conditions.
- Limited Adoption and Compatibility Issues: The effectiveness of WPA3's security improvements is limited by its adoption rate. Many devices still use older Wi-Fi security protocols due to hardware limitations or lack of firmware updates. This slow adoption rate means that many networks remain vulnerable to attacks that WPA3 is designed to mitigate.
In conclusion, while WPA3 represents a significant step forward in wireless network security, it is not without its weaknesses. Ongoing research and updates are essential to address these vulnerabilities and enhance the security of wireless networks.
Powerful advanced tool for multiple Wi-Fi networks Surveys, Analysis and Troubleshooting.
-
Get NetSpot
macOS 11+, Windows 7/8/10/11
WPA3 vs. WPA2. How does WPA3 differ from WPA2?
As mentioned above, WPA3 handles WiFi security differently. Most people connect via a WPA2 network either by sharing passwords (bad) or via WPS. WPS is convenient. Tap a button on the router at the same time as the device to connect to the device to the router, and we’re on.
The problem is WPS sends a 23-bit pin as part of the signup process. 23 bits is nothing compared to the 384-bit hashes that WPA3 uses to connect devices to routers. A clever hacker can sit there and within 9 million tries — a mere minute in computer terms — gain access to the router. Just sit, wait for the WPS signal to go out and the hacker could be in.
Then there’s the level of encryption for open networks. Going into a coffee shop or connecting a phone into the mall lets that device onto an open network. It makes sense. The inconvenience in connecting to a WiFi network with even a shared password is usually too much for a store’s customers to stand for.
The problem is that on an open wifi network, a clever hacker can listen in between the devices and try to decrypt the communications between bank websites or cashier machines. Then we’re back to unauthorized people listening in to bank passwords and credit card numbers.
WPA3 security also triumphs over WPA2 systems when it comes to open networks with an enhanced protection system. WPA3 routers use Wi‑Fi CERTIFIED Enhanced Open, meaning that even when the devices connect to the WiFi router on an open network, there is strong encryption between the device and the router.
So even if a hacker is listening in, first they have to break through the WiFi encryption, then break a totally different set between the web browser and the bank, or the specific teller machine and the financial systems they’re talking to. Nothing is absolutely secure, but making unauthorized users work twice as hard to get the information they shouldn’t have, it makes people safer all around.
| WPA2 | |
| Full name | WiFi Protected Access 2 |
| Release date | 2004 |
| Encryption method | AES-CCMP |
| Session key size | 128 bits |
| Session authentication method | Pre-Shared Key (PSK) |
| Brute force attacks | Vulnerable |
| WPA3 | |
| Full name | WiFi Protected Access 3 |
| Release date | 2018 |
| Encryption method | AES-CCMP / AES-GCMP |
| Session key size | 128 bits / 256 bits |
| Session authentication method | Simultaneous Authentication of Equals (SAE) |
| Brute force attacks | Not vulnerable |
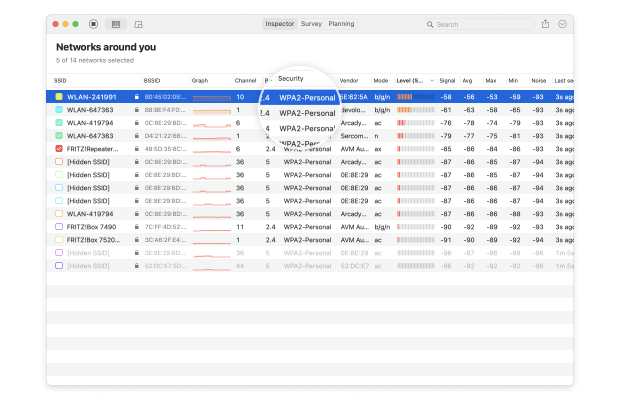
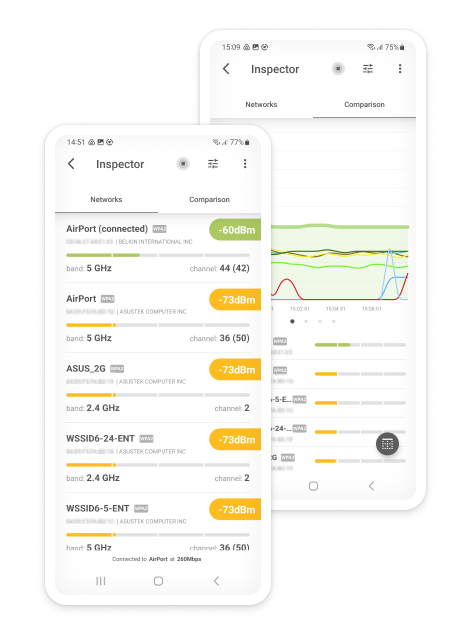
How to Check WiFi Encryption Type with NetSpot
Before connecting to an unfamiliar WiFi network, you should always check its wireless encryption status to see how well it protects your data from unauthorized third parties. This is especially important if the network is located in a public place, putting it within reach of opportunistic cybercriminals equipped with packet-sniffing tools.
Fortunately, you can easily check WiFi encryption status using NetSpot:
Launch NetSpot. The application launches in Inspector mode by default, and that’s what you need to see the WiFi security types of nearby networks.
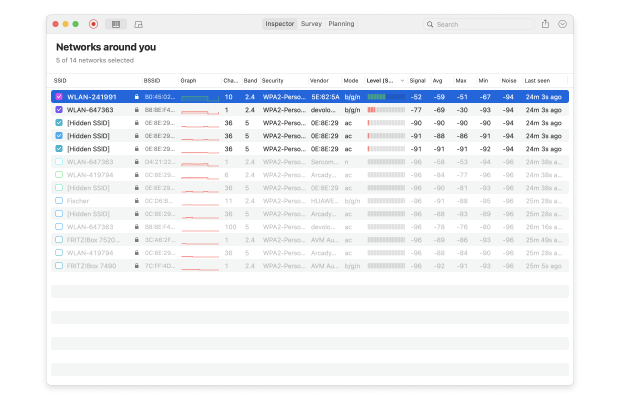
Analyze WiFi networks around you, perform wireless surveys, and test Internet speed — all with just a phone or tablet in your hands.
Conclusion
The WPA3 security standard was released in 2018 to address the latest cybersecurity threats, and it’s already supported by all WiFi 6-certified routers. Anyone who can should take advantage of it to improve their cybersecurity posture because it can be the difference between a cybersecurity incident and business as usual.
Powerful advanced tool for multiple Wi-Fi networks Surveys, Analysis and Troubleshooting.
-
Get NetSpot
macOS 11+, Windows 7/8/10/11
WPA3 FAQs
Both WPA2 (Wi-Fi Protected Access 2) and WPA3 (Wi-Fi Protected Access 3) are security certification programs developed by the Wi-Fi Alliance. WPA3 is the successor to WPA2, and it offers a number of improvements to address its predecessor’s shortcomings.
WPA3 is considerably more secure than WPA2, so you should use it whenever possible.
WPA3 Personal is one of several forms of WPA3, intended for home users rather than enterprises.
Yes, WPA3 is more secure than WPA2 because it uses Simultaneous Authentication of Equals (SAE) instead of Pre-Shared Key (PSK), among other things.
No, not all WiFi devices support WPA3. Only devices that are WiFi 6-certified are guaranteed to support the standard.
WiFi 6 routers use WPA3 to secure communication with WPA3-compatible devices, and they’re also backwards compatible with devices that support only WPA2.